Metasploit Framework (MSF)
Metasploit is primarily designed as an exploitation toolkit. It contains a variety of different modules that have prepackaged exploits for a number of vulnerabilities.
Installation
$ sudo apt update
$ sudo apt install metasploit-framework
initialize the database! (PostgreSQL) ??
$ msfdb init
$ msfconsole -q
# to check that we've connected to the database
msf6 > db_status
# to save the settings/active datastores in metasploit
msf6 > save
MetaSploit Framework architecture
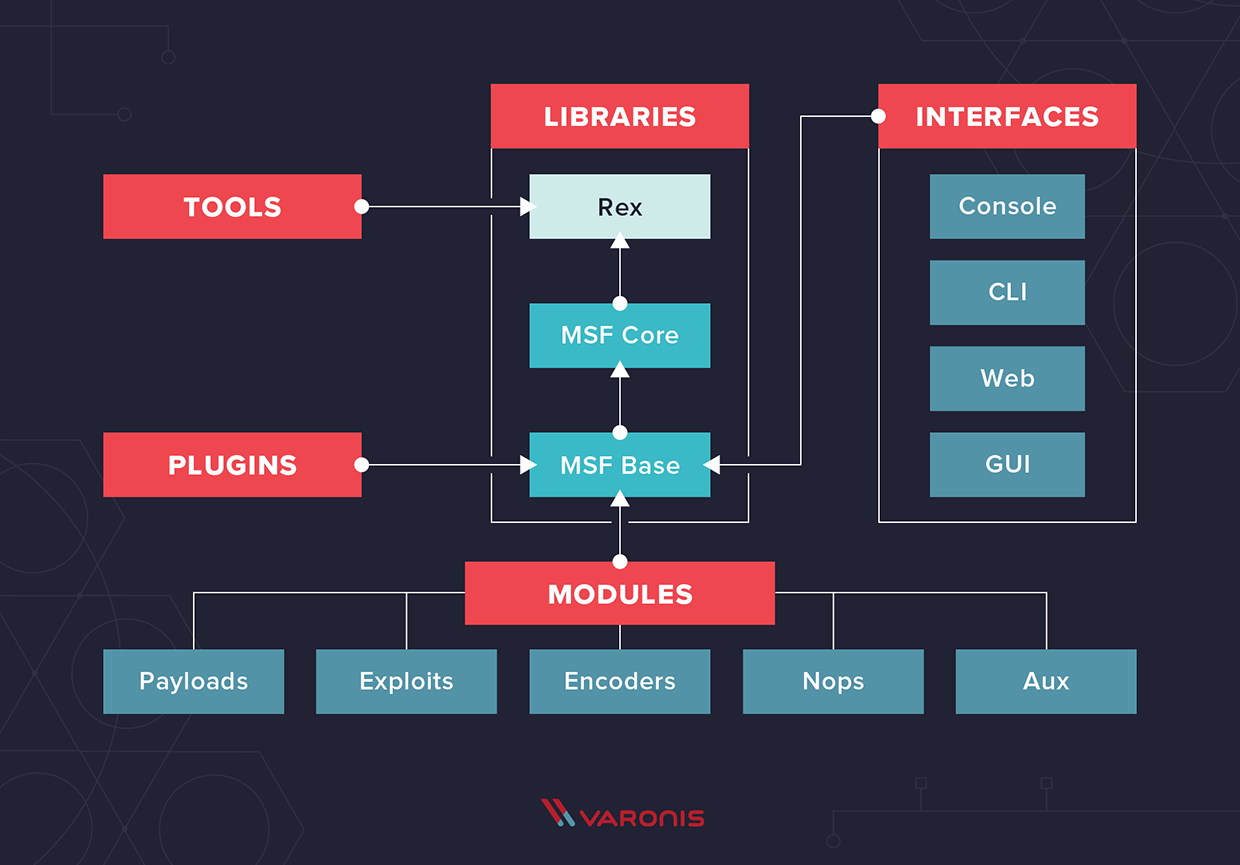
| exploit | module holds all of the exploit code |
|---|---|
| payload | Used hand in hand with exploits, contains the various bits of shellcode we send to have executed following exploitation |
| aux | commonly used in scanning and verification machines are exploitable, This is not the same as the actual exploitation of course |
| post | One of the most common activities after exploitation is looting and pivoting. Which module provides these capabilities |
| encoder | Commonly utilized in payload obfuscation, module allows us to modify the ‘appearance' of our exploit such that we may avoid signature detection |
| nop | used with buffer overflow and ROP attacks |
| load | a command to load different modules |
Searchsploit
$ searchsploit -u # updating !!
# OR some of the exploit metadata are not included. To access them,
$ searchsploit [exploitName Version] -w # Exploit-DB Online
$ searchsploit -m [exploit-db-number.ext] # mirror/copy the exploit
# Examples :
$ searchsploit afd windows local
$ searchsploit -t oracle windows
$ searchsploit -p 39446
$ searchsploit linux kernel 3.2 --exclude="(PoC)|/dos/"
$ searchsploit -s Apache Struts 2.0.0
$ searchsploit linux reverse password
$ searchsploit -j 55555 | json_pp